Now that we’ve answered “Why Tor?”, let’s take a look at how Tor actually works.
Consider the game of treasure hunt. You start off with a clue and that clue sends you somewhere. There you find another clue which sends you somewhere else and so on till you find the treasure (or get fed up and go home).
Tor doesn’t get fed up. It is software incapable of emotions. But it actually does work a bit like treasure hunt.
Breaking down the metaphor, the player travelling from clue to clue is a data packet. The clues are Tor relays or checkpoints, each point knows where you’re coming from, and where you’re going. Nothing more, nothing less. The relays don’t even know what the data packet contains since it is encrypted.
The treasure is the destination website, or whatever service you’re trying to reach. Only when the data packet has arrived at the endpoint, can it be decrypted. The destination website responds by sending it’s own data packets (encrypted such that only we can decrypt it) back through the same tunnel that leads to us.
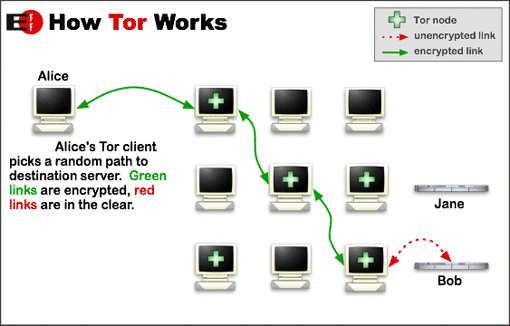
Now, Tor comes in the form of a browser and a relay client. The browser is based on Mozilla Firefox and has all the familiar functionality of Firefox. The relay client is responsible for setting up a chain of relays: nodes in the global Tor network through which our data packets will travel. This is the connection that the browser uses instead of connecting directly to the destination IP address. This tunnel is randomly assigned and changes every few minutes.
This is what makes Tor work. Broadly speaking, Tor aims to solve three privacy problems:
- First, Tor prevents websites and other services from learning your location, which they can use to build databases about your habits and interests. With Tor, your Internet connections don’t give you away by default – now you can have the ability to choose, for each connection, how much information to reveal.
- Second, Tor prevents people watching your traffic locally (such as your ISP or someone with access to your home wifi or router) from learning what information you’re fetching and where you’re fetching it from. It also stops them from deciding what you’re allowed to learn and publish – if you can get to any part of the Tor network, you can reach any site on the Internet.
- Third, Tor routes your connection through more than one Tor relay so no single relay can learn what you’re up to. Because these relays are run by different individuals or organizations, distributing trust provides more security than the old one hop proxy approach.
Today, Tor is being used by more people than ever before. . Strength in numbers. Tor hides you among the other users on the network, so the more populous and diverse the user base for Tor is, the better your anonymity.
So, that was the high level overview of Tor, now let’s take a look at exactly how the relays that form the network do their thing.
Relays
Relays are the heart of the Tor network. Currently, there are around 7000 relays routing traffic through the Tor network. These relays are located around the world and run entirely by volunteers willing to donate some bandwidth for the cause. Relays don’t need any special hardware or software to run. They just have the Tor software configured to act as a relay (You can start one up yourself right now).
When it comes to speed and anonymity of the Tor network - the more relays, the better. This makes sense, because every relay only has so much bandwidth to offer. Additionally, if there are more relays to choose from, it will be more difficult to track any one user.
Right now the path length (number of hops between you and your destination) is hard-coded at 3 plus the number of nodes in your path that are sensitive. That is, in normal cases it’s 3, but for example if you’re accessing a hidden service or a “.exit” address it could be 4. User’s can’t change their path length. There’s a couple reasons for this:
- Longer path lengths increase the load on the network without providing any more security. The middle of the path is not where attacks happen, they happen at the endpoints.
- If everyone could pick their own path lengths, it could make identification easier. “Oh look! There’s that guy that always uses 11 relays”. If everyone uses the same path length, everyone is equally anonymous.
Why specifically 3 though? Every path has 3 relays because every single relay has a specific job.
Types of Relays
- Entry/Guard Relay - This is the entry point into the Tor network. Relays are chosen to serve as guard relays after they’ve been around for a while. That is they have proven that they’re going to be stable and have high bandwidth.
- Middle Relay - Middle relays are used to transport traffic from the guard relay to the exit relay. This is what prevents the guard and exit relay from knowing about each other. The guard doesn’t know where the data is going, and the exit point doesn’t know where the data is coming from.
- Exit Relay - These relays are the exit point at the edge of the Tor network. This is where the data packets surface and reach their final destination.
That’s the gist of it. Relays have a rather complex lifecycle about which you can learn more from here.
Running a guard or middle relay is perfectly safe. All that passes through these relays is harmless encrypted data and the relays themselves remain blissfully unaware of the contents.
Running an exit node though is tricky, to say the least. Not technically, but legally. Converting a guard/middle relay to an exit one is as easy as flipping a switch. (If only government surveillance came with a switch)
The thing about running an exit node is that exit nodes connect directly with the final destination. Any illicit activity surfaces up here and if you’re the one running the exit relay, it is seen as coming from your system. So, should you be held responsible? But it’s not really your traffic, is it? Best case scenario, you just get a few DMCA notices for alleged piracy (For which Tor provides a boilerplate response). Worst case scenario, a police raid.
And with that we end our discussion on Tor relays. There’s still some things left, most notably: bridges, consensus and hidden services. But we’ll leave those for part 2 (keep an eye out!).
For now, let’s take a moment to pause and consider why we’re here to begin with. On some uneventful day, Chelsea Manning uploaded the Collateral Murder videos that passed through some of these Tor relays. On another equally slow day, Edward Snowden set up a meet with journalists by sending an encrypted email through Tor. Now we know that these couple of days ended up changing the course of history. And here we stand.
At this very moment, thousands of people, people like you and me, are using Tor out of necessity. They’re using Tor in war-torn countries, in dictatorships, because the ‘normal’ internet has been heavily censored by the government to the point of only serving propaganda. Journalists are using Tor to keep in touch with whistleblowers, people who’ve risked everything because they believe that they’re in a position to do something good. And the world rewards these people by calling them traitors, by exile or worse. They deserve better.
“All it takes for evil to triumph, is for good men to do nothing”
-Edmund Burke
Don’t do nothing. So, let’s head over to the next one and start using Tor.
Want to be a real hacker? Sign Up!



